READ ALSO: Chinese Espionage Operations and Tactics – Part 2
China’s main espionage activities in the United States are the illegal export of military and dual use technology. Of the 260 cases documented or in courts, 80 per cent occurred in the US. 43.7 per cent of these cases related to (in the US) IEEPA, EAR, and ITAR violations.
Known intelligence operations conducted by the Chinese have thrown up a basic question. What is the percentage of cases which have come to light? Is it 10 per cent or 90 per cent of Chinese operations. Quite likely the former. So, how many people are spying worldwide on behalf of the Chinese government? No one knows the answer. Yet some conclusions can be drawn.
Key Findings
There are over 600 documented cases of China’s worldwide intelligence collection efforts. Some of the major findings are:
• There has been a phenomenal expansion of its espionage efforts over the last 20 years.
• Many Chinese government agencies, People’s Liberation Army, State Owned Enterprises, private companies, individuals, and several universities are involved in conducting espionage.
• A major effort is directed towards military and space technologies.
• Predominantly (over 90 per cent) of espionage activities involve Chinese ethnic people, of whom 80 per cent are males.
• Social media is used by the Ministry of State Security (MSS) to target foreigners with access to sensitive information.
• Visa and border control system is used by the MSS to identify potential recruitments and manage clandestine assets.
• Almost half of China’s traditional espionage efforts are targeted against Taiwan (political and military secrets).
• Priority technologies have been identified in government strategic planning documents
• Made in China 2025, Space Science and Technology in China, and A Road- map to 2050, the National Key Technologies R&D Program, and the 13th Five Year Plan – for foreign science and technology collection efforts.
• China follows a ‘whole of society’ approach to espionage, which negatively affects America’s economy, diplomatic influence, and military capabilities.
• China uses espionage and coercion against government entities and business decision making to threaten European national and economic security
Legal Framework for Espionage
The CCP uses all elements of society, ie, universities, think tanks, foreign affairs departments, government sponsored overseas educational programs, military liaison programs, friendship and student associations, etc, – and through them, foreign government officials, scientists, academics, and students – to support its global espionage efforts. All Chinese government departments are required to support Ministry of State Security (MSS) intelligence operations.
China’s legal system has been moulded to ensure the intelligence apparatus can exploit private industry to gain access to foreign individuals, secrets, and technology. In 2014, 2015, and 2017, the National People’s Congress and State Council made public the requirements that all Chinese citizens and companies (operating in China or Chinese companies abroad) must collaborate in gathering intelligence.
Article 22 of the 2014 Counter-Espionage Law states that during a counter-espionage investigation, ‘relevant organizations and individuals’ must ‘truthfully provide’ information and ‘must not refuse’.
Article 7 of China’s National Intelligence Law of 2017 states that “Any organization or citizen shall support, assist and cooperate with the state intelligence work in accordance with the law, and keep the secrets of the national intelligence work known to the public. The state protects individuals and organizations that support, assist and cooperate with national intelligence work.”
Article 14 provides intelligence agencies authority to compel any entity to provide this support: “The state intelligence work organization shall carry out intelligence work according to law, and may require relevant organs, organizations and citizens to provide necessary support, assistance and cooperation.”
The National Intelligence Law Implementing Regulations, was published in November 2017, which explained that “When state security organs carry out the tasks of counter-espionage work in accordance with the law, and citizens and organizations that are obliged to provide facilities or other assistance according to the law refuse to do so, this constitutes an intention to obstruct the state security organs from carrying out the tasks of counter-espionage work according to law.”
Companies and citizens face severe punishments for noncompliance.
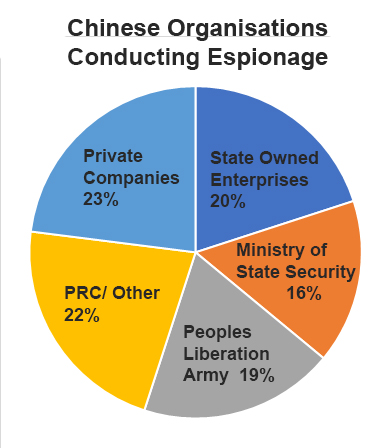
Chinese Organizations Conducting Espionage
Espionage activities correlated to their sponsoring organization (the “customer” receiving the information or technology) showed five distinct clusters of organizations engaging in espionage. The governing CCP uses government, quasi-government, academic, and commercial entities as mechanisms to conduct all forms espionage abroad. Most interesting of these are China’s ‘non-traditional collectors’ which include State Owned Enterprises, universities, and private companies. The employment of such a broad set of entities for intelligence collection indicates China’s ‘whole of society’ approach to espionage.
China’s Ministry of State Security or Ministry of State Security (MSS) was formed in June 1983.
Central Military Commission (CMC) Joint Staff Department, Intelligence Bureau (formerly 2 PLA) is responsible for collecting and analyzing foreign military intelligence including technology.
People’s Liberation Army (PLA) collection capabilities include military attaches conducting overt and clandestine collection, students, and other collectors under government and commercial covers.
There are 150,000 State Owned Enterprises (SOE) of which 50,000 are owned by the central government and include aerospace and defense companies, subordinate research institutes, and technology transfer organizations. In 2018, Xi Jinping directed all SOEs to amend their bylaws to ensure the concepts of service to the CCP keeping national and economic security above profit.
Some private companies and individuals indulge in illegal exports or trade secrets for commercial benefit. University are often involved in establishing shadow labs to copy foreign research and commercial production facilities to replicate foreign material and technology.
Other PRC government elements like PLA Political Department Liaison Office, United Front Work Department (UFWD) and many universities under the State Administration for Science, Technology, and Industry for National Defense (SASTIND) work for espionage.
SASTIND
SASTIND assigns research projects to ministries with military production responsibilities and manages military acquisition requirements for the CMC’s Equipment Department. SASTIND has two departments (Comprehensive Planning Department and the International Cooperation Department) responsible for developing and tasking technology related intelligence requirements, and for collecting intelligence related to them. MSS and PLA Joint Intelligence Bureau are also involved.
SASTIND also has direct supervision over seven universities as well as contracts for defense research with 55 additional universities. As many as 35 institutes and universities are on the US Department of Commerce Entities List for their research in support of Chinese defense entities involved in the theft of technologies.
There is a near equal distribution of espionage activities between the four major organizational clusters (MSS, SOE, PLA, Private Companies).
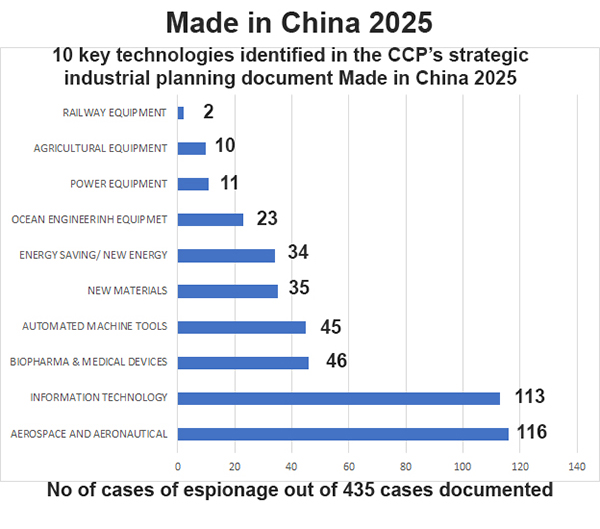
Aerospace & Aeronautical Equipment
China strongly focuses on collection of foreign aerospace and aeronautical equipment. The primary collectors are the PLA Joint Intelligence Bureau and private companies conducting export violations, and individuals (Insider Threats) working in foreign aerospace companies.
Key technologies stolen or attempted are: Cryogenic pumps for space vehicles, valves, transfer lines, refrigeration equipment, space qualified radiation hardened circuits, components for the storage and use of liquid hydrogen, cryogenic coolers, Ka-band space communications, satellite/missile insulation blankets – germanium coated polyimide film, and multi octave travelling wave tubes used as amplifiers in satellite transponders. Major systems include the Space Shuttle, Delta IV Rocket, F-15 Fighter, C-17 transport, F-22 Fighter, F-35 Fighter, B-1 Bomber, Ch 46/47 Chinook, C-130 training equipment and much more.
Information Technology
Information technology is a high priority target with strong emphasis on advanced semiconductors and manufacturing technology. The US restricted semiconductor sales to the Chinese company ZTE for evading sanctions on Iran and North Korea and repeatedly lying to Department of Commerce officials and lifted the ban after the company paid a $1 billion fine and agreed to reprimand its Board. Chinese company Huawei faces charges of espionage in the United States, Germany, and Poland.
Key information technology objectives include microelectronics, microwave integrated circuits, microprocessors, circuit boards, crypto key devices, data and voice transmission systems, semiconductors, and trade secrets such as laser manufacturing techniques.
Analysis of Espionage Cases
China’s dominant espionage activities overseas are economic espionage, and export control violations. Half of them are related to ITAR, EAR, IEEPA, covert action, research violations in high-tech sectors.
Next is economic espionage. Traditional espionage comprises one-fourth of all espionage activity.
‘Silicon Valley’ in northern California is the number one spot for China’s illegal technology collection efforts.
Information technology, aerospace and aeronautical equipment takes priority over automated machine tools and robotics.
Research universities are also primary targets for collection efforts most often accomplished through talent programs (i.e. Thousand Talents Program, Hundred Talents Program, etc.). In numerous cases, professors, graduate students, and PLA researchers have also been arrested stealing research from overseas universities for use in China.
Chinese spies have used public and commercial encryption, hosting meetings in China to avoid detection, dead drops, covert communications) and use of third countries for meetings.
Surprisingly a number of cases have been detected where the Ministry of State Security demonstrated no discernible tradecraft in agent recruitment, tasking, communications, and data transfer with no significant attempt to hide the activity.
READ ALSO: Chinese Espionage Operations and Tactics – Part 2