China’s Defense Budget Surges 7.2% to $249 Billion, Far Ahead of India
China has announсed a 7.2% inсrease in its defense budget, reaсhing $249 billion, signifiсantly outpaсing India's spending, whiсh is about $78.8 billion. This surge...
NUCLEAR WEAPONS – How Pakistan Sustains Its N-weapons Supply Chain
Smart Nuclear Fuel Processing at Khushab Complex
Pakistan's Khushab nuclear complex, located in Punjab province, sits at the heart of the country's weapons-grade plutonium production...
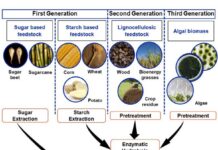
Global Bio-Fuel Alliance – G-20 Summit New Delhi
Introduction
With population of India touching 140 billion and having undergone a rapid and sustained economic expansion in the last 10 years, demand for energy...
Green Hydrogen – Transformative Fuel For The Future
Introduction
In the visionary words of the Indian Prime Minister spoken from the ramparts of Red Fort on 15 Aug 2021, ‘Not only will Green...
Virtual Reality and Data (Part 1)
A National Security Perspective
Virtual Reality (VR), often projected as a future state of current tech improvisation, is, on the contrary, one of the earliest...
Boardroom Spymaster
Countering Private Intelligence Companies
Archisman Goswami
Once more, as in centuries past, wars are rather easily started and then fought without perceptible restraint – remarked noted...
Anti-India Forces at Work
With Prosperity Comes Rivalry
A range of actors are working to undermine India's unity and integrity. These forces include foreign governments and organizations that support...
Proven Cases of Espionage in the US
READ ALSO: Chinese Espionage Operations and Tactics – Part 1
Chinese Espionage Operations and Tactics – Part 2
Case of Edward Peng Xuehua
Edward Peng Xuehua's case exposed...
Series of CT Summits Held in Nov 22-Jan 23
India Places High Priority to Counter-Terrorism
India-Central Asia Meeting of NSAs
At the first India-Central Asia meeting of NSAs/secretaries of security councils, involving Kazakhstan, Kyrgyzstan, Tajikistan,...
Peng Cheng Laboratory
One Among 19 Cyber Ranges in China
With government funding, massive computational capacity, and ties to the military, Peng Cheng Lab is likely to be...