What to Expect in 2023?
India, US, Indonesia, and China accounted for 45% of total cyberattacks on government agencies worldwide in the second half of 2022, according to a report by cybersecurity firm CloudSek, released on 30 December. The number of attacks on government agencies were up 95% year-on-year, the report claimed.
The government itself has acknowledged that 18 million cyberattacks and 200,000 online threats daily in the first quarter of 2022.
India was the most targeted country in 2022 as attacks on government agencies more than doubled. CloudSek attributed this to an increase in activities of Malaysia-based hacktivist group Dragon Force, which ran campaigns such as #OpIndia and #OpsPatuk against India in retaliation to the controversial comments by an Indian politician on Prophet Mohammed.
Another hacker group Khalifah Cyber Crew intensified attacks on India in protest against alleged “Muslim discrimination” by the government, the report said.
Attacks on government agencies in China declined to 4.5% of all attacks from 13.10% last year. On the other hand, in India, US, and Indonesia, the share of all attacks grew from 6.3% to 13.7%, 7.4% to 9.6%, and 4.6% to 9.3%, respectively.
CERT-In Data
Government data, collated by the Ministry of Electronics and Information Technology’s Indian Computer Emergency Response Team (CERT-In), is available only till 2021, but that too shows an increase in cyberattacks in India.
In 2019, CERT-In handled close to 3,94,499 incidents in total, in which it suggested remedial measures for organisations and shared notes on “cyber threats and vulnerabilities”. In the same year, CERT-In issued 204 security alerts and 38 advisories.
The number of incidents handled by CERT-In surged in 2020 to 11,58,208, a near-tripling over the previous year. This surge continued in 2021, which saw 14,02,809 incidents, a 21 per cent increase.
The matters CERT-In looks into include website intrusion and malware propagation, malicious code, phishing, distributed denial-of-service (DDoS) attacks, website defacements, unauthorised network scanning or probing activities, ransomware attacks, data breaches and vulnerable services.
Trends
The Indian Computer Emergency Response Team said: “Threat actors were leveraging tools that are already available in the cyber environment rather than making custom tools and malwares. By this way, they were being able to bypass many security controls.”
Threat actors are also able to execute scripts that reboot victim’s machine into ‘safe mode’, and thus bypass security solutions.
In terms of mitigation, the agency recommended victims to immediately disconnect and isolate infected systems from the network. IT also recommended to turn off any wireless internet connectivity and isolate all system backups.
Spike in Ransomware Attacks in India
In a first of its kind report, the Indian Computer Emergency Response Team (CERT-In) said that it had observed a 51 percent increase in ransomware incidents in the country in the first half of the business year (H1) in 2022.
The information technology sector was the most affected when it came to these attacks, CERT-In said, followed by manufacturing and finance.
CERT-In attributed the rise in attacks in India to Djvu, a ‘high-risk’ virus that majorly targets citizens. The agency also named Phobos, a ransomware which “strikes smaller companies and individuals that have less capacity to pay relative to larger businesses”, to have played a role in the increase.
It also attributed the increase to Hive, a year-old ransomware which has grown into one of the most prevalent ransomware payloads in the ransomware-as-a-service (RaaS) ecosystem, according to Microsoft.
“Ransomware as a Service”
A ransomware is a type of malicious software designed to block access to a computer system until a sum of money is paid. Ransomware as a service (RaaS) is a subscription-based model that enables affiliates to use already-developed ransomware tools to execute ransomware attacks, said Upguard, a cybersecurity company.
In the report CERT-In said, “Ransomware-As-A-Service (RAAS) ecosystem is evolving with sophisticated double and triple extortion tactics and a wide range of ransomware campaigns through affiliates.”
“This is leading to higher probability of monetization and further rise in attack campaigns. Post covid accelerated digitalisation and hybrid work culture are also aiding this threat emergence,” it added.
Modus Operandi
The agency noted that ransomware gangs were focusing on penetrating known unpatched vulnerabilities of public facing applications for gaining entry into the network.
“Compromised credentials of remote access services (VPN/ RDP) are being used by threat actors to gain entry into the network,” it said.
Apart from that, CERT-In said phishing campaigns are also another major source of ransomware infections.
Zerofox describes a phishing campaign as a scam created by cybercriminals to steal financial resources or sensitive data from victims using manipulative emails or other fraudulent digital assets.
State of Affairs
In recent times the three most notorious members of the ransomware family- Ryuk, Purga, and Stop made major headlines in the nation.
The Stop ransomware caused about 10.10% of the ransomware attacks followed by Ryuk making about 5.84% attacks along with Purga for deploying 0.80% of ransomware attacks
Ryuk seemed to have been the most active threat landscape in the Indian public as well as private sectors. On the other hand, brute-force attacks on RDP and SMBs seemed to have steadily increased in the last five years.
According to Forbes, there was one ransomware attack every 10 seconds in 2020.
Reportedly, organizations have faced double extortion in 2020 across the globe. Moreover, the cost of ransomware damage is predicted to hit around $20 billion by 2021.
Although, this figure may vary later depending upon the cost of attacks and their devastating consequences. To know how brutal ransomware attacks can get, here are the top devastating ransomware attacks that took place in India.
Hacktivism
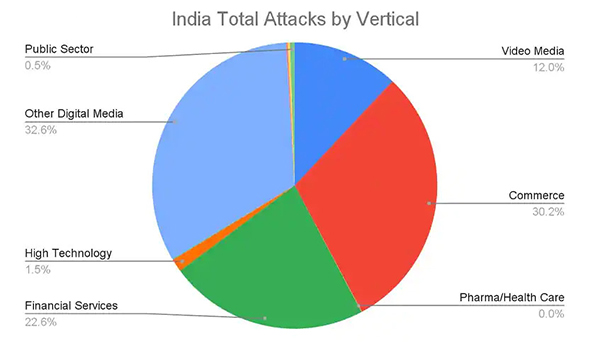
In 2022, hacktivism accounted for 9% of the cyberattacks on the government sector. Hacktivism is a form of cyberattack where the hacker’s motivation is not financial gains but to promote a political agenda or protest against certain policies. Last year, attacks on China also increased due to its aggressive stance towards Taiwan and the Uyghur community.
In addition to hacktivism, government agencies in India are also increasingly being targeted by phishing campaigns, according to the report.
Ransomware Attacks
CloudSek also found that ransomware groups were very active and accounted for 6% of the attacks on governments. LockBIT, which provides ransomware-as-a-service (RaaS) was the most prominent ransomware operator. Its targets in 2022 included government agencies in the US, Canada, and Italy. In November, a Russian national was arrested in Canada for alleged involvement in LockBIT ransomware campaigns in the US.
In November 2022, India’s top government-run hospital All India Institute of Medical Science (AIIMS) was also hit by a cyberattack causing disruption of online services that lasted over two weeks. India’s nodal cybersecurity agency Computer Emergency Response Team (CERT-In) found in its investigation that five AIIMS’ servers were compromised during the attack and nearly 1.3 terabytes of data was encrypted by hackers.
What to Expect in 2023
Experts believe that state-sponsored hackers will go after cloud services in 2023 due to growing digital transformation. “Nation states will begin to target cloud service provider (CSP) managed services as companies migrate more of their attack surface to these managed services,” according to Bob Huber, chief security officer at Tenable, a cybersecurity firm.
India’s had its worst year of cyberattacks, but 2023 will see govt & firms ramp up defences
India was a top target for cyberattacks in 2022, shows study by web security firm Indusface. As govt tries to address policy vacuum, companies likely to spend more on cybersecurity.
According to a study released Tuesday by Indusface, a Tata Capital-funded software-as-a-service (SaaS) security firm, India has become one of the most attacked and breached countries in the world. Among the 829 million cyber-attacks detected and blocked globally by the firm in the fourth quarter of 2022, close to 59 per cent were directed towards India.
In this backdrop, what will the government and companies do differently in the coming year?
As the government readies its legislation on cybersecurity, numerous industry-wide surveys and sector experts say that 2023 will see companies spending significant amounts to secure their digital systems from attacks.
According to Sajan Paul, managing director & country manager, India & SAARC, Juniper Networks, a “zero trust” policy will be an “essential security strategy” for India, going forward. ‘Zero trust’ model assumes breach and verifies each request as though it originates from an open network.
Data protection Bill and CERT-In rules
India’s IT ministry has come up with the Digital Personal Data Protection Bill, 2022, defining some roles of data fiduciaries and introducing appellate committees that will deal with redressals and grievances. Many have termed it a “step in the right direction” to ensure data security.
The draft law, alongside CERT-In rules, has been part of core policy discussions in India. The rules now require companies to report cybersecurity incidents within six hours. While this seems stringent, it might not be practical, some experts believe. This was perhaps the most significant development in the cybersecurity domain in 2022.
Commentary
Cyberattacks on government agencies are not new. Many of these attacks state sponsored and are aimed at stealing sensitive information or cripple critical infrastructure of other countries. Indian entities are often targeted by hacker groups with links to China. Similarly, many of the attacks on US agencies often originate from Russia or North Korea.
According to IBM’s ‘Cost of Data Breach Report 2022’, the average cost of data breaches in the government sector has increased from $1.93 million in 2021 to $2.07 million this year.
Threat actors have modernised their attack methodologies, evolved sophisticated tactics and adopted a wide range of attack campaigns.
==
Top Six Attacks in 2020-21
Telangana and AP Power
A malicious software attacked the power utility systems of Telangana and Andhra Pradesh in 2020 where all the servers went down until the glitch was rectified. Since the computer systems of Telangana and Andhra Pradesh power utilities were interlinked, the virus attack quickly spread, taking down all the systems.
UHBVN Ransomware Attack
Uttar Haryana Bijli Vitran Nigam was hit by a ransomware attack where the hackers gained access to the computer systems of the power company and stole the billing data of customers. The attackers demanded Rs.1 crore or $10 million in return for giving back the data.
WannaCry
India was the third worst-hit nation by WannaCry ransomware, affecting more than 2 lakh computer systems. During the first wave of attacks, this ransomware attack had hit banks in India including few enterprises in Tamil Nadu and Gujarat. The ransomware majorly affected the US healthcare system and a well-known French car manufacturing firm.
Mirai Botnet Malware Attack
This botnet malware took over the internet, targeting home routers and IoT devices. This malware affected 2.5 million IoT devices including a large number of computer systems in India. This self-propagating malware was capable of using exploitable unpatched vulnerabilities to access networks and systems.
Petya
India was one of the top 10 countries to be hit by Petya ransomware. This ransomware attack halted work at one of the terminals of India’s largest seaport causing computer lockdown and serious consequences for the country’s exports.
BSNL Malware Attack
The state-owned telecom operator BSNL was hit by a major malware attack, impacting nearly 2000 broadband modems! 60,000 modems became dysfunctional after the malware attack hit the Telecom Circle.